Maturity Cycle
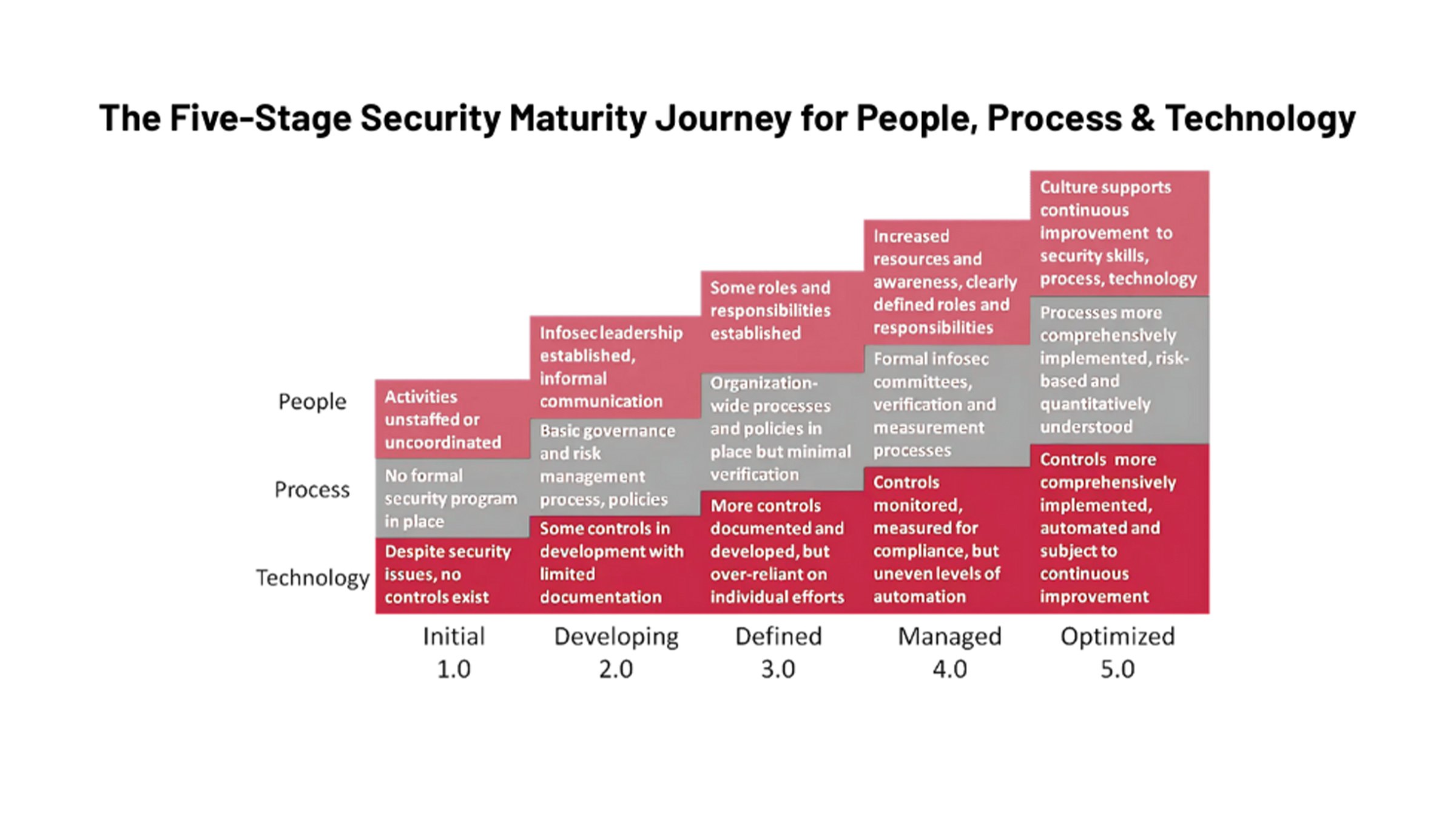
It is important to note that the maturity cycle is just a general intended pattern toward a more robust security program. The specific tasks, the order they are executed and the time frame across which they are deployed have to be tied to the specific risks and objectives of the individual organization.
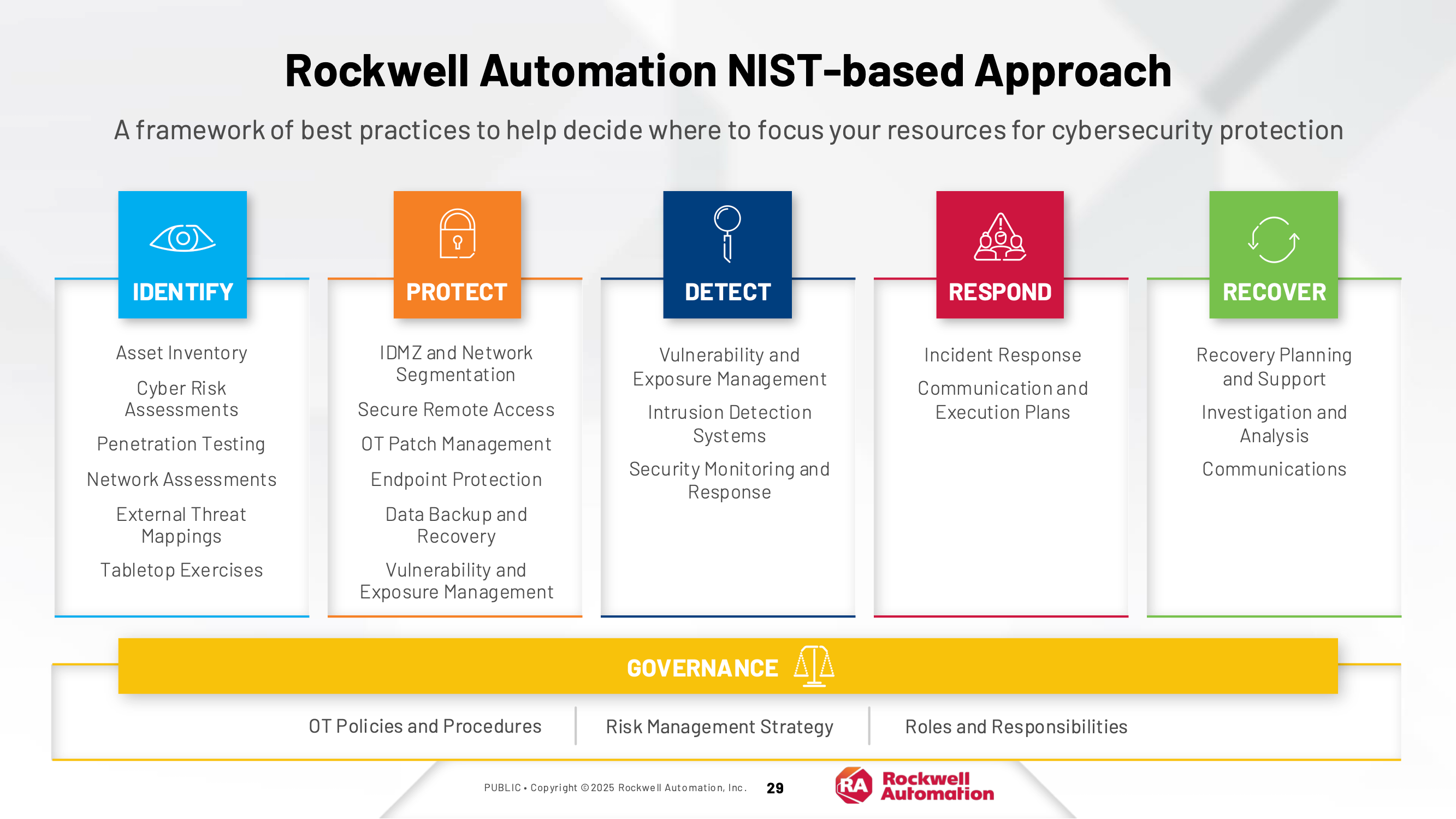
Step 3: Execute Foundational Initiatives
As highlighted above, every program should have a set of foundational initiatives necessary to enable the broader program. These initiatives should provide some rapid impact on security while also providing baseline capabilities.
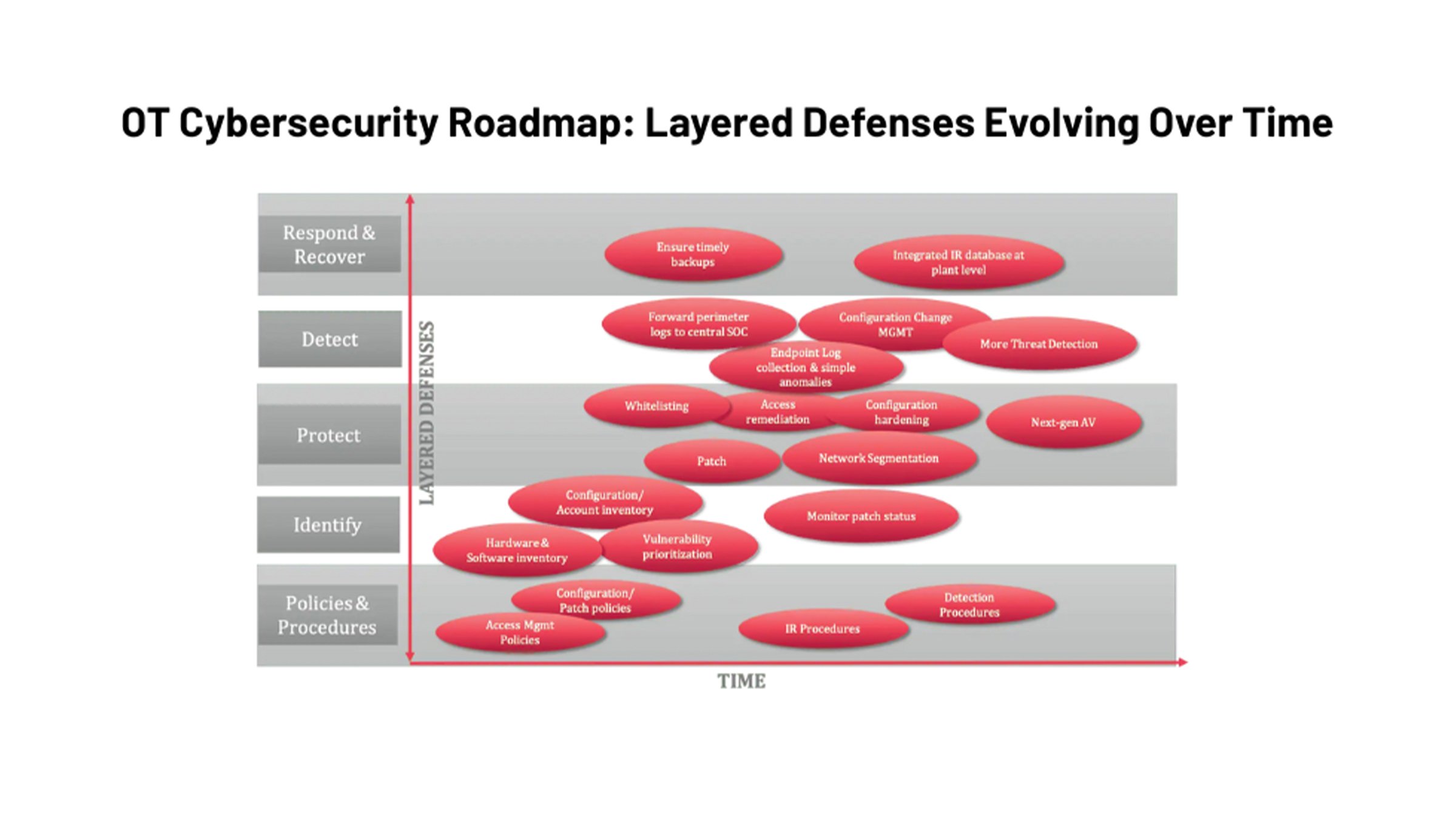
This first “wave” of initiatives should be items that can be achieved within 90 days to demonstrate progress as well as allow for rapid movement to additional elements. These initiatives will include both “informational” or “baselining” initiatives as well as the first wave of “remediation” or “hardening” activities. The baselining-type of activities would include hardware and software inventory, configuration baselines, firewall rule maps, etc. The remediation-type activities would likely include software removal, hardening of baselines, or initial segmentation.
These initiatives normally have “corporate” and “site-level” components. In geographically dispersed organizations, they will focus on approximately 3-5 pilot sites representing a range of locations for the “site-level” components. The foundational initiatives will be rolled out at these sites and they will act as “lead dogs” to be ahead of the pack in implementing greater levels of maturity over time.
This first phase of execution will likely include several key elements:
- Central components such as policies on sensitive data or password standards, procedures such as management of change or patching, and technology such as a central reporting functionality.
- Site-level components such as asset inventory, configuration baselines, and network design/ segmentation reviews.
- Establishing key decision points such as which controls will not apply to certain assets, decision-making on risk-reward or cost-benefit trade-offs, and rules for “technical feasibility exceptions” where devices such as PLCs or older HMIs may not be able to meet control standards and will require some form of compensating controls.
Foundational initiatives can strengthen supply chain risk management efforts (SCRM) through:
- Secure software development practices, like vulnerability scanning and code reviews, to reduce the risk of introducing vulnerabilities into your system from third parties.
- Requiring software bill of materials generation (SBOM) from your vendors to provide visibility of the components within your software. This enables you to identify and address vulnerabilities from third parties quickly.
- Configuration baselines for your organization and vendor systems to confirm that third-party systems meet your security requirements.
- Regular scanning and patching to improve your overall security and reduce entryways for threat actors.
- Integrating supply chain into your incident response plan to address cyber incidents that extend from third-party vendors.
Step 4: Build on Foundation
With version 1.1, most organizations rolled out proven tool sets to additional sites, embarked on second or third-phases of security tool and procedure design, testing, and deployment to pursue a rich, multi-layered security program.
Organizations that implement NIST CSF 2.0 are more than likely in the refining, building depth, and maturing phases. Keep the following in mind as you continue to scale your security program with additional processes and technologies:
- Automate routine tasks where possible.
- Continue to reiterate and optimize for process improvement.
- Maintain a thorough integration framework for new infrastructure.
- Confirm that your employees are up to speed on the latest training.
- Regularly update priorities based on risks and business needs.
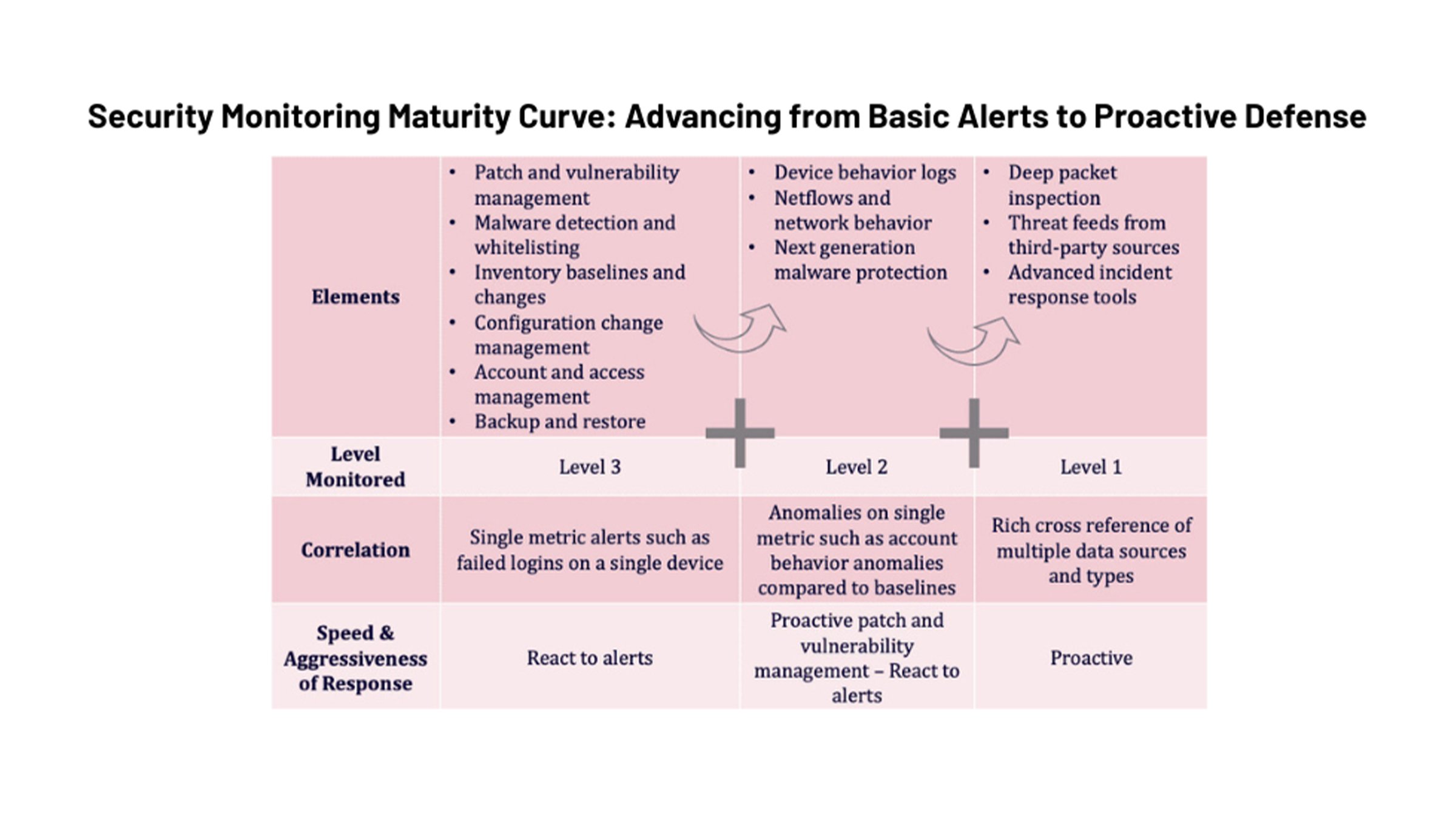
Step 5: Monitor, Measure, and Improve