The ‘Framework Core’ offers accessible cybersecurity guidance with six primary functions: Govern, Identify, Protect, Detect, Respond, and Recover. Each function has detailed categories and subcategories, like Asset Management under Identify, guiding organizations to inventory resources. It also includes references, standards, and guidelines to establish cybersecurity baselines and communicate status to stakeholders.
1. Govern
The “Govern” function maintains the organizations risk management strategy. It provides the direction for how an organization handles the outcomes from the remaining five functions.
What it includes:
- Establishment and communication of OT cybersecurity policies.
- Coordinate and align OT cybersecurity roles and responsibilities.
- Educate on and manage legal and regulatory requirements.
- Incorporate cybersecurity risks into corporate risk management processes.
- Implement continuous oversight and checkpoints on ongoing initiatives
2. Identify
The “Identify” function is the second step in the NIST Cybersecurity Framework. It involves understanding an organization’s assets, its business context, governance, and assessing risks.
What it includes:
- Asset Management: Creating an inventory of all assets.
- Business Environment: Understanding the organization’s context and strategic goals.
- Governance and Risk Management: Establishing policies for risk management.
- Risk Assessment: Identifying cybersecurity risks.
- Supply Chain Risk Management: Assessing third-party risks.
This function lays the groundwork for effective cybersecurity risk management by helping IT or OT security managers gain visibility into their enterprise networks and ICS so they know which infrastructure needs extra protection. For organizations, it informs decision-making and ensures alignment with strategic goals.
3. Protect
The “Protect” function focuses on safeguarding assets and data from cybersecurity threats through measures like access control, data security, awareness and training, and security policies.
What it includes:
- Access Control: Controlling access to critical systems.
- Data Security: Protecting data through encryption and secure storage.
- Awareness and Training: Providing cybersecurity training.
- Security Policies and Procedures: Implementing cybersecurity policies.
- Incident Response Planning: Preparing for security incidents.
- Secure Supply Chain Management: Ensuring third-party security.
Protecting assets and data is paramount for maintaining data integrity, confidentiality, and availability. These measures are instrumental in helping IT or OT security managers safeguard access controls for critical systems and secure industrial equipment configurations to reduce the overall attack surface and ensure the organization’s resilience.
4. Detect
The “Detect” function emphasizes early and effective detection of cybersecurity events, including monitoring for unusual activities and incidents.
What it includes:
- Anomalies and Events: Monitoring for unusual activities.
- Security Continuous Monitoring: Real-time threat detection.
- Incident Detection and Response: Responding to security incidents.
- Detection Processes: Formalized processes for detecting and reporting events.
- Threat Intelligence Sharing: Sharing threat information.
Early detection is essential for identifying threats promptly. It allows IT or OT security managers to respond quickly, contain incidents, and minimize damage and downtime, ultimately improving cybersecurity risk management.
5. Respond
The “Respond” function involves actions taken after detecting a cybersecurity incident, including incident response planning, coordination, analysis, mitigation, recovery, and communication.
What it includes:
- Incident Response Planning: Preparing for incident responses.
- Incident Coordination and Communication: Coordinating responses and communication.
- Incident Analysis: Understanding the incident’s nature and scope.
- Incident Recovery: Restoring affected systems.
- Coordination with Law Enforcement: Collaborating with law enforcement.
This function also helps IT or OT security managers develop an aligned and clear incident response plan that maintains stakeholder trust. The result is effective action that can limit impact, restore normal operations, and comply with legal and regulatory requirements.
6. Recover
The “Recover” function focuses on restoring services and operations after a cybersecurity incident, including recovery planning, coordination, communication, and lessons learned.
What it includes:
- Recovery Planning: Developing and maintaining recovery plans.
- Recovery Coordination: Coordinating recovery efforts.
- Communication and Reporting: Transparent communication.
- Lessons Learned: Identifying areas for improvement.
A swift and efficient recovery process helps IT or OT security managers limit downtime, return to normal business functionality, and bolster the organization’s resilience.
NIST CSF Profiles
What is a NIST CSF Profile?
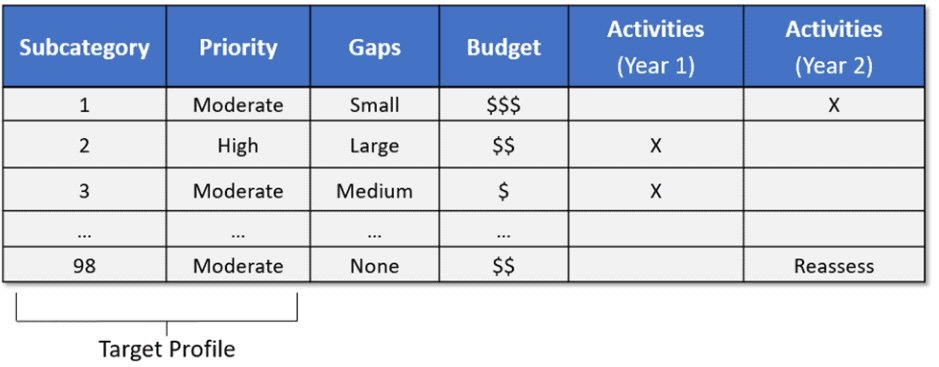
In essence, NIST CSF Profiles are your customized roadmaps. This means you can tailor the framework's outcomes to your specific risks, business objectives (i.e., uptime), and available resources. You can also compare your current and target profiles to gain a clear, prioritized action list that strengthens your security posture across both domains.
How do NIST CSF Profiles Work?
Here’s how it works:
Selecting Outcomes: Organizations choose specific cybersecurity outcomes from various categories and subcategories provided by the NIST framework. These outcomes represent what they want to achieve in terms of cybersecurity.
Customization: The selected outcomes are tailored to fit the organization’s unique needs. This customization takes into account the organization’s business objectives, risk tolerance, available resources, and current cybersecurity practices.
Comparison: Organizations create two profiles—a ‘Current’ Profile reflecting their existing cybersecurity activities and a ‘Target’ Profile representing their ideal cybersecurity state. By comparing these two profiles, they can see the gaps between their current practices and their desired level of cybersecurity.
Why are NIST CSF Profiles Helpful?
Profiles are helpful for several reasons:
Customization: They allow organizations to adapt the NIST framework to their specific circumstances. This acknowledges that every organization has different goals, risks, and available resources.
Clarity: Profiles provide a clear roadmap, making it easy for organizations to understand what cybersecurity improvements they need to make.
Prioritization: Organizations can prioritize their efforts by identifying gaps between the ‘Current’ and ‘Target’ Profiles. They know which areas require immediate attention to enhance their cybersecurity posture.
Alignment: Profiles help align cybersecurity activities with the organization’s overall business objectives. This allows cybersecurity efforts to support and enhance the organization’s mission.
In summary, a Profile is a tailored plan that helps organizations set specific cybersecurity goals, customize their approach, and prioritize actions to improve their cybersecurity practices. It allows organizations to align their cybersecurity efforts with the organization’s unique needs and objectives.